Home » Cyber Security
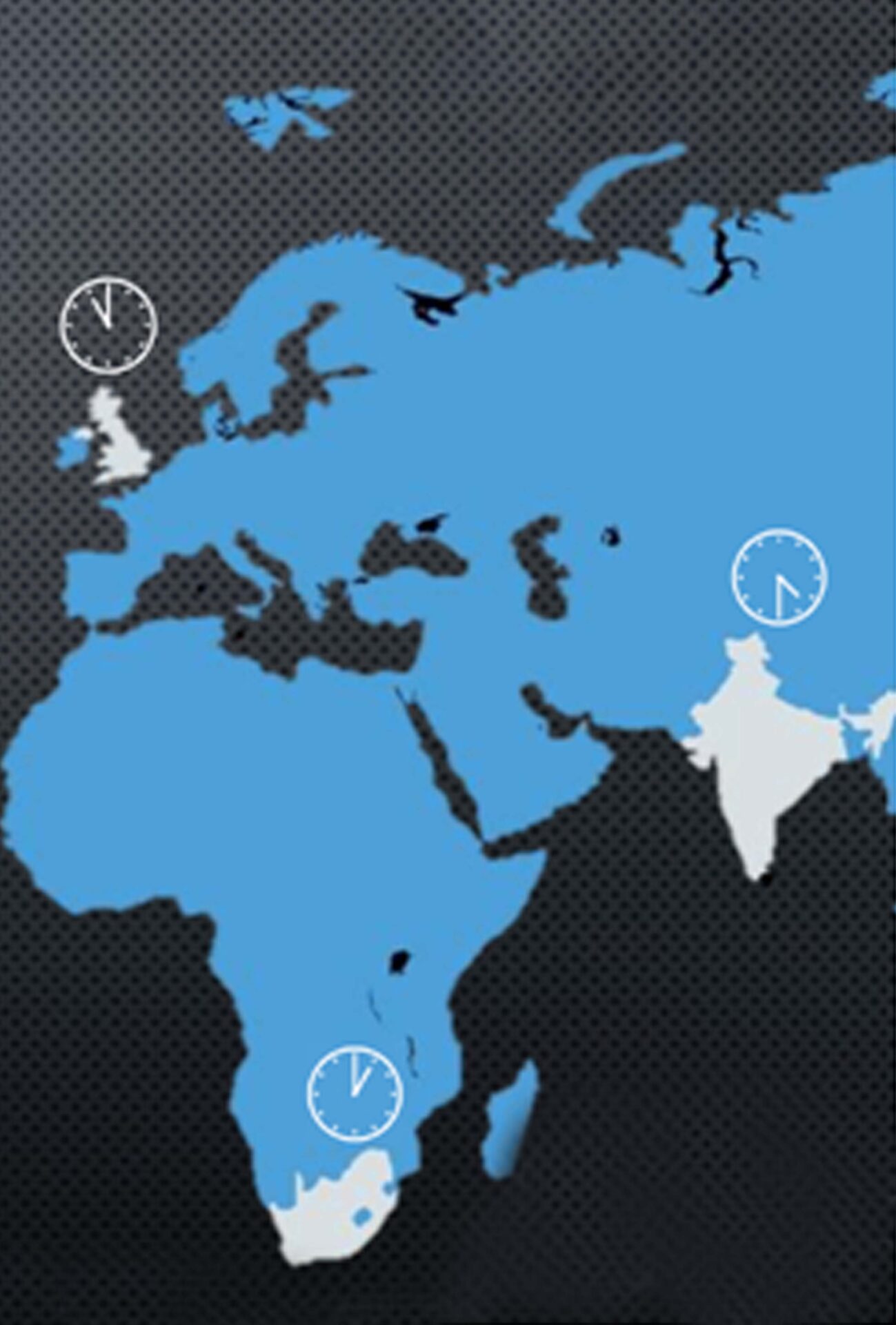
We are a Managed Security Services Provider (MSSP) Specializing in Managed Detection and Response Services through our global, 24×7 cybersecurity operations centers in the UK, South Africa and India with a dedicated Blue Team.
We also have strong skills and experience in Identity Governance and Administration (IGA), Privileged Account Management (PAM), Access Management Solutions and Autonomous Pen testing.
Vetted NCSC CCP certified architects are available for bespoke projects, secure framework assessment and advisory.
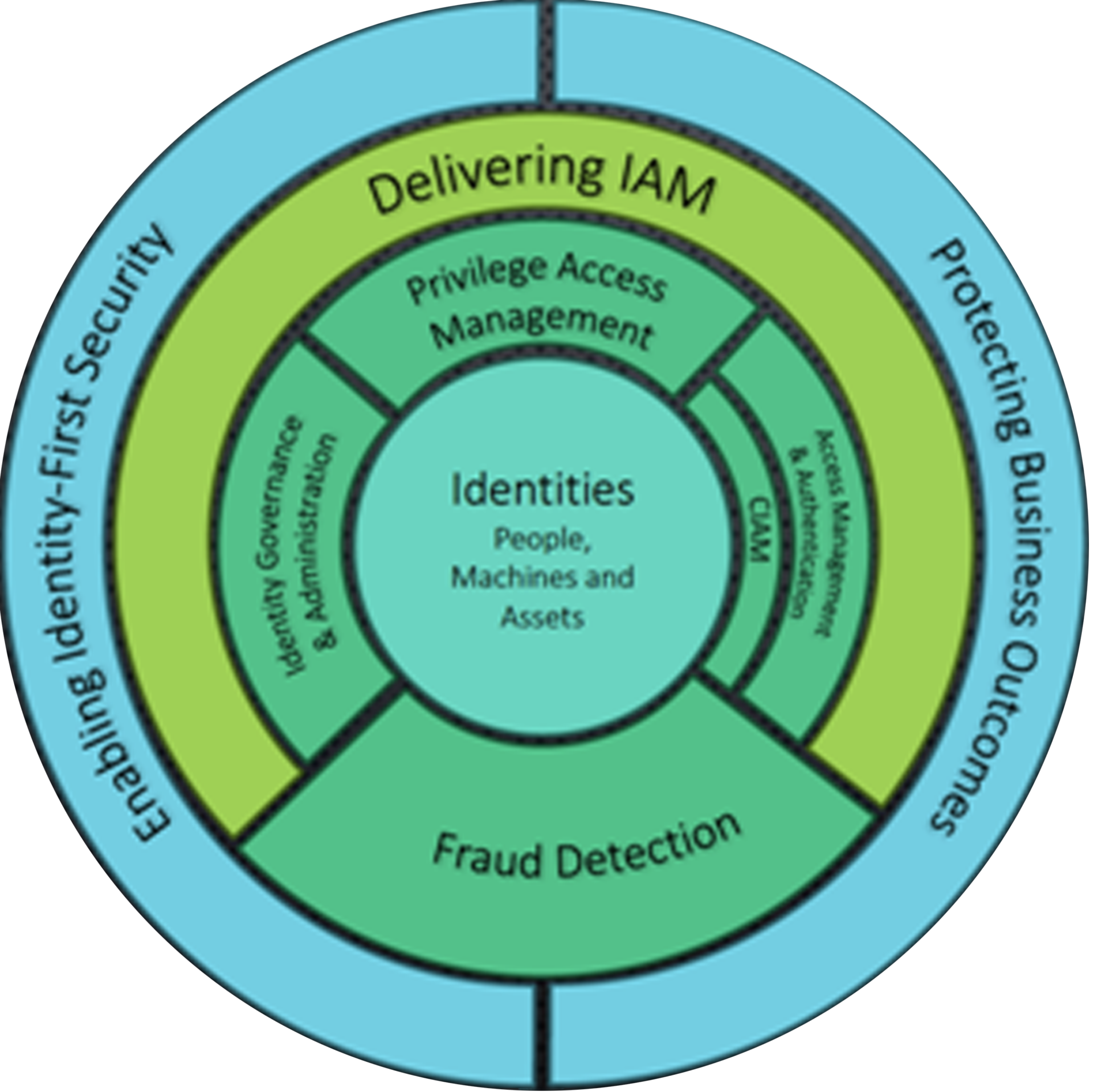
Administrate and provision accounts and entitlements, govern identity life cycles for entities such as people and machines, and use analytics to help automate and cut down on manual processes.
Verify that humans and machines are who or what they claim, and ensure that they are entitled to securely access web resources in line with zero-trust principles (via authorization and adaptive access)
Provide a user-friendly, secure and scalable foundation to enable external users to interact with applications and services.
Establish and run an effective long-term program for implementing IAM practices, processes and technologies that are aligned with business objectives.
Deploy a journey-time orchestrated stack of identity- proofing, identity-affirmation and fraud-detection capabilities to mitigate the risks of account opening and account takeover fraud while maintaining a great user experience.
© 2024 DeepX All Rights Reserved.